Research Strengths
The Institute is actively engaged with both the private and public sectors in a variety of basic research and problem-driven research activities in the program areas listed below. The goal of basic research is to achieve fundamental breakthroughs in the science of cybersecurity. The Institute takes a longer-term view with the objective of making key advances in the creation of a national-scale hacker-resistant information infrastructure whereas problem-driven research projects seek solutions to hard problems of a near-term nature.
The Institute is engaged with many corporations seeking research solutions to exceedingly difficult and complex cybersecurity problems. This class of research represents a win-win, such that the corporations receive solutions to problems that make a difference to their operations, while Institute researchers (faculty, post-doctoral and student) receive satisfaction that their solutions are making a difference in today’s information-centric environment.
Hardware and Network Security Engineering
 This program focuses on hardware and networking security research projects, including both conventional and emerging technology research endeavors. With respect to hardware security research, there are two principal categories of security threats: intentional and non-intentional. Intentional threats are due to purposely-introduced circuit functionality or hardware malware that allow exploitation to occur. Non-intentional threats exploit design flaws or unspecified behavior.
This program focuses on hardware and networking security research projects, including both conventional and emerging technology research endeavors. With respect to hardware security research, there are two principal categories of security threats: intentional and non-intentional. Intentional threats are due to purposely-introduced circuit functionality or hardware malware that allow exploitation to occur. Non-intentional threats exploit design flaws or unspecified behavior.
Network security engineering largely overlaps with hardware security engineering at the lower physical and data link layers, and both hardware and networking systems heavily leverage similar operational models. Network security projects at the higher layers are also within the domain of this program. Finally, this program also engages in research involving emerging technologies that have direct impact on cybersecurity such as quantum information processing and reversible computing.
Software and Systems Security
 This broadly scoped program tackles a host of challenges related to software and systems security, including software assurance, trustworthy systems, privacy-preserving technologies, and cybersecurity analytics. Modern software systems are exceedingly complex and must work correctly in the face of error, mischance, or malicious corruption. The scope of this program encompasses software and systems issues ranging from those found within large data centers and high performance computing installations to small embedded systems.
This broadly scoped program tackles a host of challenges related to software and systems security, including software assurance, trustworthy systems, privacy-preserving technologies, and cybersecurity analytics. Modern software systems are exceedingly complex and must work correctly in the face of error, mischance, or malicious corruption. The scope of this program encompasses software and systems issues ranging from those found within large data centers and high performance computing installations to small embedded systems.
Autonomous Systems
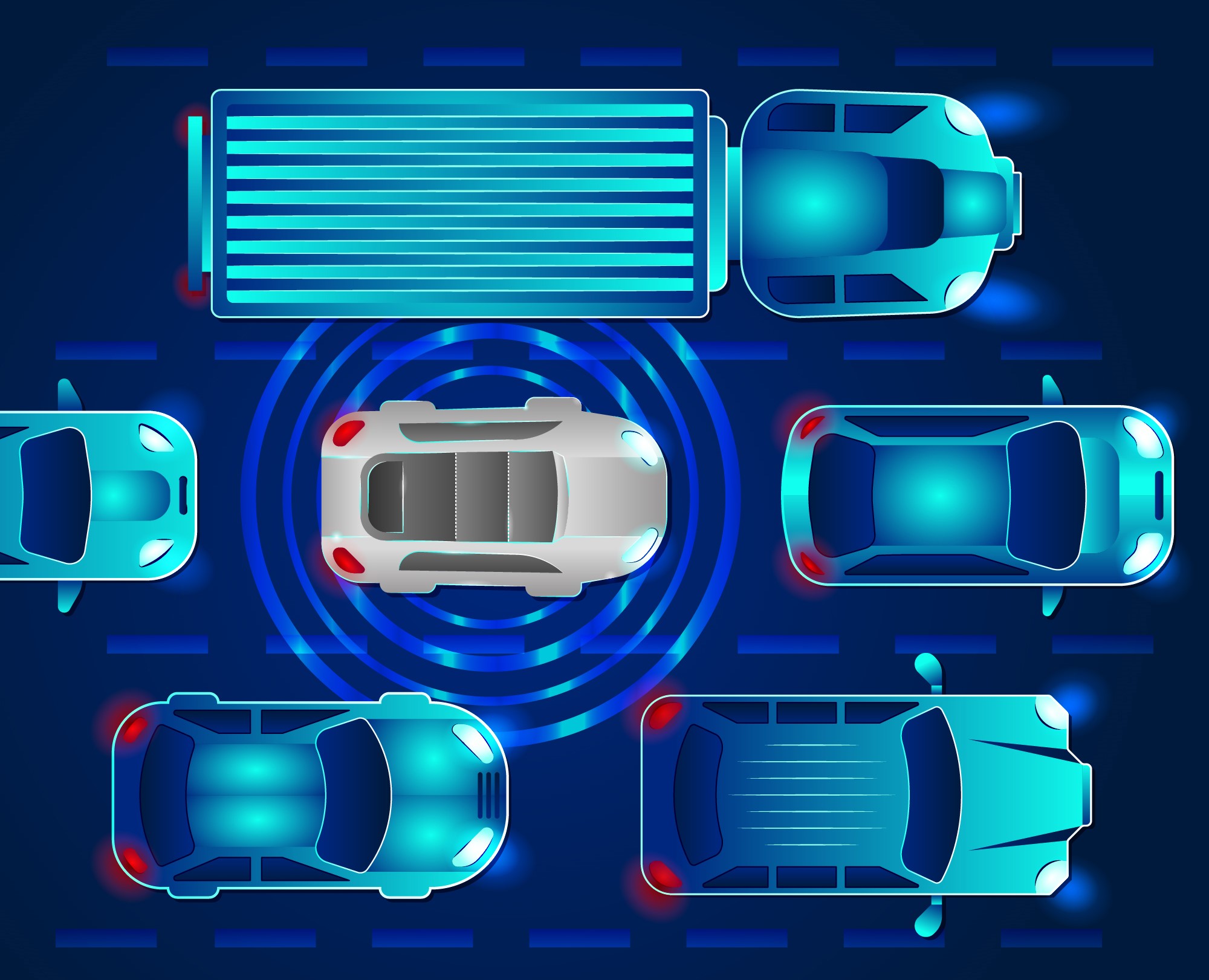
Autonomous Systems are sensor-laden, situationally-aware, able to communicate, and able to make decisions without human involvement. These systems include driverless vehicles and 5G/6G towers. They are enabled by sensors, machine learning and/or artificial intelligence, and 5G wireless networks. However, using machine learning and artificial intelligence expands the attack surface of an autonomous system. The system is vulnerable to traditional attacks and new classes of cyber attacks. For example, a new class of cyber-attacks is ‘poisoning’ machine learning training data with the effect of corrupting or weakening it.
The SMU Darwin Deason Institute for Cyber Security’s Cyber Autonomy Range (CAR) is a one of a kind facility built to ensure that these autonomous systems will be better able to withstand such cyber attacks.
Artificial Intelligence, Machine Learning, and Data Science
 Artificial intelligence (AI) revolutionizes research in cybersecurity by enhancing threat detection, response, and mitigation strategies. AI enables analysis of vast amounts of data for identifying patterns indicative of cyber threats, enabling proactive defense measures. AI-powered systems can autonomously adapt and evolve to counter new and sophisticated attacks in real-time, augmenting human analysts’ capabilities. The Deason Institute for cyber security continues to innovate and quantify these threats through novel AI/ML approaches, including anomaly detection, side channel investigation, and sensor analysis. Additionally, AI assists in predicting potential vulnerabilities and recommending preventive measures to fortify systems. However, the evolving nature of AI-driven cyber threats necessitates continuous refinement and innovation in cybersecurity research to stay ahead of malicious actors.
Artificial intelligence (AI) revolutionizes research in cybersecurity by enhancing threat detection, response, and mitigation strategies. AI enables analysis of vast amounts of data for identifying patterns indicative of cyber threats, enabling proactive defense measures. AI-powered systems can autonomously adapt and evolve to counter new and sophisticated attacks in real-time, augmenting human analysts’ capabilities. The Deason Institute for cyber security continues to innovate and quantify these threats through novel AI/ML approaches, including anomaly detection, side channel investigation, and sensor analysis. Additionally, AI assists in predicting potential vulnerabilities and recommending preventive measures to fortify systems. However, the evolving nature of AI-driven cyber threats necessitates continuous refinement and innovation in cybersecurity research to stay ahead of malicious actors.
Quantum Engineering and Informatics Applications

The Darwin Deason Institute is engaged in quantum informatics research, a widely-recognized emerging source of threats in cyber security. As quantum computers are predicted to make current secure communications methods (cryptographic methods) obsolete soon, DDI researchers are developing new and novel quantum photonic integrated circuits that will support next-generation cryptographic applications. DDI researchers are also actively involved in developing new algorithms to support applications such as quantum data science and software tools to support development of new quantum computing algorithms.
SMU now offers an M.S. in Quantum Engineering. This comprehensive program delves into quantum informatics and quantum engineering, enabling you to create and improve advanced processes, systems, and devices. For more information please see https://www.smu.edu/lyle/departments/ece/ms-in-quantum-engineering
